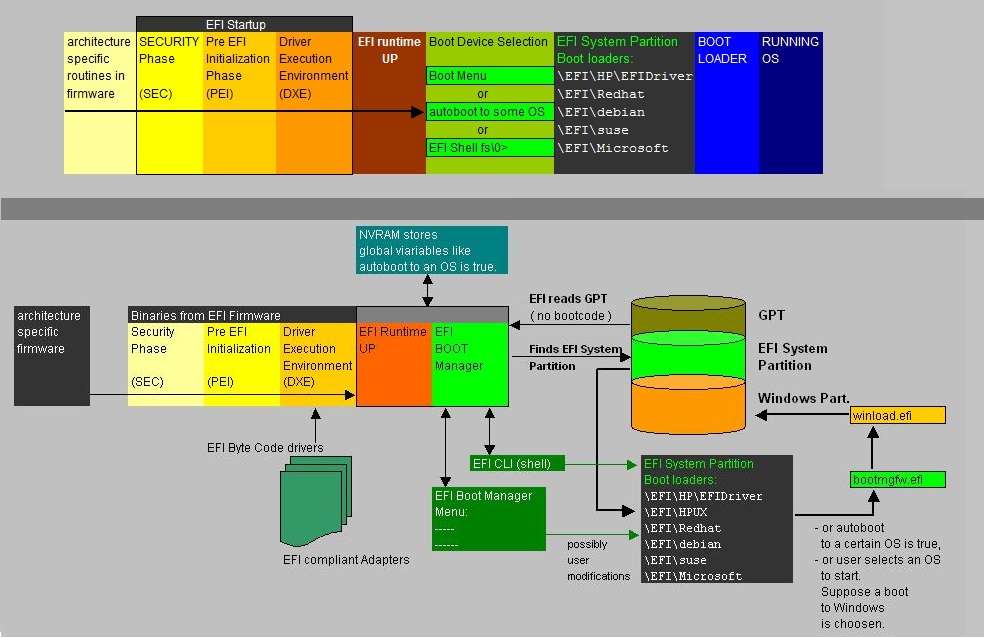
| Command: |
Comments: |
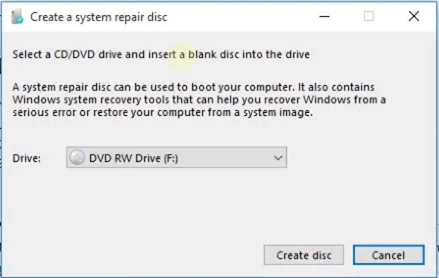
| F:\> diskpart |
Let's start a "diskpart" session |
| DISKPART> select disk 0 |
We need to focus diskpart on DISK0 |
| DISKPART> list volume |
We need to see which partitions are on DISK0 |
| DISPART> select volume "number" |
Select the "number" of the EFI partition |
| DISKPART> assign |
The EFI partition now has a drive letter. Let's assume it's "E:". |
| DISKPART> exit |
We may leave diskpart right now. |
| F:\> e: |
Change the drive to E: (the EFI partition). |
| E:\> cd \EFI\Microsoft\Boot |
Go to the boot directory. |
| E:\> bootrec /fixboot |
Repair the Boot Record. |
| E:\> attrib -r -h -s bcd |
Optional: it's possible, before you can rename the bcd, you must modify the attributes first. |
| E:\> ren BCD BCD.save |
Let's make a save copy (via rename) of the BCD store, before we recreate it. |
| E:\> bcdboot c:\Windows /l en-us /s E: /f All |
Here we assume Windows is on C: and the locale is US English. |